目錄
安裝helm3
https://github.com/helm/helm/releases
tar -zxvf helm-v3.13.1-linux-amd64.tar.gz
mv linux-amd64/helm /usr/local/bin/helm
root@k8s-master71u:~# helm version
version.BuildInfo{Version:"v3.13.1", GitCommit:"3547a4b5bf5edb5478ce352e18858d8a552a4110", GitTreeState:"clean", GoVersion:"go1.20.8"}
配置chart 儲存庫
## 添加chart儲存庫
helm repo add gitlab https://charts.gitlab.io
## 驗證源
helm repo list
##查詢可以安裝的gitlab-runner chart
helm search repo -l gitlab/gitlab-runner
root@k8s-master71u:~# helm repo add gitlab https://charts.gitlab.io
"gitlab" has been added to your repositories
root@k8s-master71u:~# helm repo list
NAME URL
rancher-stable https://releases.rancher.com/server-charts/stable
jetstack https://charts.jetstack.io
prometheus-community https://prometheus-community.github.io/helm-charts
gitlab https://charts.gitlab.io
root@k8s-master71u:~# helm search repo -l gitlab/gitlab-runner
NAME CHART VERSION APP VERSION DESCRIPTION
gitlab/gitlab-runner 0.63.0 16.10.0 GitLab Runner
gitlab/gitlab-runner 0.62.1 16.9.1 GitLab Runner
gitlab/gitlab-runner 0.62.0 16.9.0 GitLab Runner
gitlab/gitlab-runner 0.61.3 16.8.1 GitLab Runner
gitlab/gitlab-runner 0.61.2 16.8.0 GitLab Runner
gitlab/gitlab-runner 0.61.1 16.8.0 GitLab Runner
gitlab/gitlab-runner 0.61.0 16.8.0 GitLab Runner
gitlab/gitlab-runner 0.60.1 16.7.1 GitLab Runner
gitlab/gitlab-runner 0.60.0 16.7.0 GitLab Runner
gitlab/gitlab-runner 0.59.3 16.6.2 GitLab Runner
gitlab/gitlab-runner 0.59.2 16.6.1 GitLab Runner
gitlab/gitlab-runner 0.59.1 16.6.0 GitLab Runner
gitlab/gitlab-runner 0.59.0 16.6.0 GitLab Runner
gitlab/gitlab-runner 0.58.2 16.5.0 GitLab Runner
gitlab/gitlab-runner 0.58.1 16.5.0 GitLab Runner
gitlab/gitlab-runner 0.58.0 16.5.0 GitLab Runner
gitlab/gitlab-runner 0.57.2 16.4.2 GitLab Runner
gitlab/gitlab-runner 0.57.1 16.4.1 GitLab Runner
gitlab/gitlab-runner 0.57.0 16.4.0 GitLab Runner
gitlab/gitlab-runner 0.56.3 16.3.3 GitLab Runner
gitlab/gitlab-runner 0.56.2 16.3.2 GitLab Runner
gitlab/gitlab-runner 0.56.1 16.3.1 GitLab Runner
gitlab/gitlab-runner 0.56.0 16.3.0 GitLab Runner
gitlab/gitlab-runner 0.55.3 16.2.3 GitLab Runner
gitlab/gitlab-runner 0.55.2 16.2.2 GitLab Runner
gitlab/gitlab-runner 0.55.1 16.2.1 GitLab Runner
gitlab/gitlab-runner 0.55.0 16.2.0 GitLab Runner
gitlab/gitlab-runner 0.54.1 16.1.1 GitLab Runner
gitlab/gitlab-runner 0.54.0 16.1.0 GitLab Runner
gitlab/gitlab-runner 0.53.3 16.0.3 GitLab Runner
gitlab/gitlab-runner 0.53.2 16.0.2 GitLab Runner
gitlab/gitlab-runner 0.53.1 16.0.1 GitLab Runner
gitlab/gitlab-runner 0.53.0 16.0.0 GitLab Runner
gitlab/gitlab-runner 0.52.1 15.11.1 GitLab Runner
gitlab/gitlab-runner 0.52.0 15.11.0 GitLab Runner
gitlab/gitlab-runner 0.51.1 15.10.1 GitLab Runner
gitlab/gitlab-runner 0.51.0 15.10.0 GitLab Runner
gitlab/gitlab-runner 0.50.1 15.9.1 GitLab Runner
gitlab/gitlab-runner 0.50.0 15.9.0 GitLab Runner
gitlab/gitlab-runner 0.49.3 15.8.3 GitLab Runner
gitlab/gitlab-runner 0.49.2 15.8.2 GitLab Runner
gitlab/gitlab-runner 0.49.1 15.8.1 GitLab Runner
gitlab/gitlab-runner 0.49.0 15.8.0 GitLab Runner
gitlab/gitlab-runner 0.48.3 15.7.4 GitLab Runner
gitlab/gitlab-runner 0.48.2 15.7.3 GitLab Runner
gitlab/gitlab-runner 0.48.1 15.7.2 GitLab Runner
gitlab/gitlab-runner 0.48.0 15.7.0 GitLab Runner
gitlab/gitlab-runner 0.47.3 15.6.3 GitLab Runner
gitlab/gitlab-runner 0.47.2 15.6.2 GitLab Runner
gitlab/gitlab-runner 0.47.1 15.6.1 GitLab Runner
gitlab/gitlab-runner 0.47.0 15.6.0 GitLab Runner
gitlab/gitlab-runner 0.46.1 15.5.1 GitLab Runner
gitlab/gitlab-runner 0.46.0 15.5.0 GitLab Runner
gitlab/gitlab-runner 0.45.2 15.4.2 GitLab Runner
gitlab/gitlab-runner 0.45.1 15.4.1 GitLab Runner
gitlab/gitlab-runner 0.45.0 15.4.0 GitLab Runner
gitlab/gitlab-runner 0.44.3 15.3.3 GitLab Runner
gitlab/gitlab-runner 0.44.2 15.3.2 GitLab Runner
gitlab/gitlab-runner 0.44.1 15.3.1 GitLab Runner
gitlab/gitlab-runner 0.44.0 15.3.0 GitLab Runner
gitlab/gitlab-runner 0.43.2 15.2.2 GitLab Runner
gitlab/gitlab-runner 0.43.1 15.2.1 GitLab Runner
gitlab/gitlab-runner 0.43.0 15.2.0 GitLab Runner
gitlab/gitlab-runner 0.42.0 15.1.0 GitLab Runner
gitlab/gitlab-runner 0.41.1 15.0.1 GitLab Runner
gitlab/gitlab-runner 0.41.0 15.0.0 GitLab Runner
gitlab/gitlab-runner 0.40.1 14.10.1 GitLab Runner
gitlab/gitlab-runner 0.40.0 14.10.0 GitLab Runner
gitlab/gitlab-runner 0.39.1 14.9.2 GitLab Runner
gitlab/gitlab-runner 0.39.0 14.9.0 GitLab Runner
gitlab/gitlab-runner 0.38.2 14.8.3 GitLab Runner
gitlab/gitlab-runner 0.38.1 14.8.2 GitLab Runner
gitlab/gitlab-runner 0.38.0 14.8.0 GitLab Runner
gitlab/gitlab-runner 0.37.3 14.7.1 GitLab Runner
gitlab/gitlab-runner 0.37.2 14.7.0 GitLab Runner
gitlab/gitlab-runner 0.37.1 bleeding GitLab Runner
gitlab/gitlab-runner 0.37.0 14.7.0 GitLab Runner
gitlab/gitlab-runner 0.36.1 14.6.1 GitLab Runner
gitlab/gitlab-runner 0.36.0 14.6.0 GitLab Runner
gitlab/gitlab-runner 0.35.3 14.5.2 GitLab Runner
gitlab/gitlab-runner 0.35.2 14.5.2 GitLab Runner
gitlab/gitlab-runner 0.35.0 14.5.0 GitLab Runner
gitlab/gitlab-runner 0.34.2 14.4.2 GitLab Runner
gitlab/gitlab-runner 0.34.1 14.4.1 GitLab Runner
gitlab/gitlab-runner 0.34.0 14.4.0 GitLab Runner
gitlab/gitlab-runner 0.33.3 14.3.4 GitLab Runner
gitlab/gitlab-runner 0.33.2 14.3.3 GitLab Runner
gitlab/gitlab-runner 0.33.1 14.3.2 GitLab Runner
gitlab/gitlab-runner 0.33.0 14.3.0 GitLab Runner
gitlab/gitlab-runner 0.32.0 14.2.0 GitLab Runner
gitlab/gitlab-runner 0.31.0 14.1.0 GitLab Runner
gitlab/gitlab-runner 0.30.0 14.0.0 GitLab Runner
gitlab/gitlab-runner 0.29.0 13.12.0 GitLab Runner
gitlab/gitlab-runner 0.28.0 13.11.0 GitLab Runner
gitlab/gitlab-runner 0.27.0 13.10.0 GitLab Runner
gitlab/gitlab-runner 0.26.0 13.9.0 GitLab Runner
gitlab/gitlab-runner 0.25.0 13.8.0 GitLab Runner
gitlab/gitlab-runner 0.24.0 13.7.0 GitLab Runner
gitlab/gitlab-runner 0.23.0 13.6.0 GitLab Runner
gitlab/gitlab-runner 0.22.0 13.5.0 GitLab Runner
gitlab/gitlab-runner 0.21.1 13.4.1 GitLab Runner
gitlab/gitlab-runner 0.21.0 13.4.0 GitLab Runner
gitlab/gitlab-runner 0.20.2 13.3.2 GitLab Runner
gitlab/gitlab-runner 0.20.1 13.3.1 GitLab Runner
gitlab/gitlab-runner 0.20.0 13.3.0 GitLab Runner
gitlab/gitlab-runner 0.19.4 13.2.4 GitLab Runner
gitlab/gitlab-runner 0.19.3 13.2.3 GitLab Runner
gitlab/gitlab-runner 0.19.2 13.2.2 GitLab Runner
gitlab/gitlab-runner 0.19.1 13.2.1 GitLab Runner
gitlab/gitlab-runner 0.19.0 13.2.0 GitLab Runner
gitlab/gitlab-runner 0.18.3 13.1.3 GitLab Runner
gitlab/gitlab-runner 0.18.2 13.1.2 GitLab Runner
gitlab/gitlab-runner 0.18.1 13.1.1 GitLab Runner
gitlab/gitlab-runner 0.18.0 13.1.0 GitLab Runner
gitlab/gitlab-runner 0.17.2 13.0.2 GitLab Runner
gitlab/gitlab-runner 0.17.1 13.0.1 GitLab Runner
gitlab/gitlab-runner 0.17.0 13.0.0 GitLab Runner
gitlab/gitlab-runner 0.16.2 12.10.3 GitLab Runner
gitlab/gitlab-runner 0.16.1 12.10.2 GitLab Runner
gitlab/gitlab-runner 0.16.0 12.10.1 GitLab Runner
gitlab/gitlab-runner 0.15.1 12.9.1 GitLab Runner
gitlab/gitlab-runner 0.15.0 12.9.0 GitLab Runner
gitlab/gitlab-runner 0.14.0 12.8.0 GitLab Runner
gitlab/gitlab-runner 0.13.1 12.7.1 GitLab Runner
gitlab/gitlab-runner 0.13.0 12.7.0 GitLab Runner
gitlab/gitlab-runner 0.12.0 12.6.0 GitLab Runner
gitlab/gitlab-runner 0.11.0 12.5.0 GitLab Runner
gitlab/gitlab-runner 0.10.1 12.4.1 GitLab Runner
gitlab/gitlab-runner 0.10.0 12.4.0 GitLab Runner
gitlab/gitlab-runner 0.9.1 12.3.0 GitLab Runner
gitlab/gitlab-runner 0.9.0 12.3.0 GitLab Runner
gitlab/gitlab-runner 0.8.0 12.2.0 GitLab Runner
gitlab/gitlab-runner 0.7.0 12.1.0 GitLab Runner
gitlab/gitlab-runner 0.6.1 12.0.1 GitLab Runner
gitlab/gitlab-runner 0.6.0 12.0.0 GitLab Runner
更新配置資訊
目前我的gitlab版本是12.3.9,所以runner我就安裝12.4的,CHART版本就是0.10.0
NAME CHART VERSION APP VERSION DESCRIPTION
gitlab/gitlab-runner 0.10.0 12.4.0 GitLab Runner
## 獲取相關版本的chart包
helm fetch gitlab/gitlab-runner --version=0.10.0
[root@zeyang-nuc-service ~]# ls
Desktop es
Documents gitlab-runner-0.15.0.tgz
## 獲取相關版本的chart包
root@k8s-master71u:~# helm fetch gitlab/gitlab-runner --version=0.10.0
root@k8s-master71u:~# ll
-rw-r--r-- 1 root root 11744 Mar 31 09:16 gitlab-runner-0.10.0.tgz
root@k8s-master71u:~# tar -xzvf gitlab-runner-0.10.0.tgz
root@k8s-master71u:~# cd gitlab-runner/
root@k8s-master71u:~/gitlab-runner# ll
total 52
drwxr-xr-x 3 root root 190 Mar 31 09:18 ./
drwx------ 13 root root 4096 Mar 31 09:18 ../
-rwxr-xr-x 1 root root 2973 Oct 21 2019 CHANGELOG.md*
-rwxr-xr-x 1 root root 345 Oct 21 2019 Chart.yaml*
-rwxr-xr-x 1 root root 796 Oct 21 2019 CONTRIBUTING.md*
-rwxr-xr-x 1 root root 1782 Oct 21 2019 .gitlab-ci.yml*
-rwxr-xr-x 1 root root 362 Oct 21 2019 .helmignore*
-rwxr-xr-x 1 root root 1084 Oct 21 2019 LICENSE*
-rwxr-xr-x 1 root root 1305 Oct 21 2019 NOTICE*
-rwxr-xr-x 1 root root 229 Oct 21 2019 README.md*
drwxr-xr-x 2 root root 4096 Mar 31 09:18 templates/
-rwxr-xr-x 1 root root 11896 Oct 21 2019 values.yaml*
values.yml
root@k8s-master71u:~/gitlab-runner# cat values.yaml
## GitLab Runner Image
##
## By default it's using gitlab/gitlab-runner:alpine-v{VERSION}
## where {VERSION} is taken from Chart.yaml from appVersion field
##
## ref: https://hub.docker.com/r/gitlab/gitlab-runner/tags/
##
image: gitlab/gitlab-runner:alpine-v12.4.0
## 鏡像下載策略
imagePullPolicy: IfNotPresent
## Gitlab伺服器地址
gitlabUrl: http://192.168.1.55/
## runner註冊token
runnerRegistrationToken: "BmSnpmSVS3CMxQ9Vyiki"
## 終止之前註銷所有跑步者
unregisterRunners: true
## 當停止管道時等待其作業終止時間
terminationGracePeriodSeconds: 3600
## Set the certsSecretName in order to pass custom certficates for GitLab Runner to use
## Provide resource name for a Kubernetes Secret Object in the same namespace,
## this is used to populate the /home/gitlab-runner/.gitlab-runner/certs/ directory
## ref: https://docs.gitlab.com/runner/configuration/tls-self-signed.html#supported-options-for-self-signed-certificates
##
# certsSecretName:
## 配置最大並發作業數
concurrent: 10
## 新作業檢查間隔
checkInterval: 30
## GitlabRunner日誌級別 debug, info, warn, error, fatal, panic
logLevel: info
## Configure GitLab Runner's logging format. Available values are: runner, text, json
## ref: https://docs.gitlab.com/runner/configuration/advanced-configuration.html#the-global-section
##
# logFormat:
## For RBAC support:
##rbac:
## create: true
## ## Define specific rbac permissions.
## resources: ["pods", "pods/exec", "secrets"]
## verbs: ["get", "list", "watch", "create", "patch", "delete"]
rbac:
create: true
rules:
- resources: ["configmaps","events","pods","pods/attach","pods/exec","secrets","services",]
verbs: ["get", "list", "watch", "create", "patch", "update", "delete"]
- apiGroups: [""]
resources: ["pods/exec"]
verbs: ["create", "patch", "delete"]
## Run the gitlab-bastion container with the ability to deploy/manage containers of jobs
## cluster-wide or only within namespace
clusterWideAccess: false
## Use the following Kubernetes Service Account name if RBAC is disabled in this Helm chart (see rbac.create)
##
# serviceAccountName: default
## Specify annotations for Service Accounts, useful for annotations such as eks.amazonaws.com/role-arn
##
## ref: https://docs.aws.amazon.com/eks/latest/userguide/specify-service-account-role.html
##
# serviceAccountAnnotations: {}
## Configure integrated Prometheus metrics exporter
## ref: https://docs.gitlab.com/runner/monitoring/#configuration-of-the-metrics-http-server
metrics:
enabled: true
## Configuration for the Pods that that the runner launches for each new job
##
runners:
## Default container image to use for builds when none is specified
##
image: ubuntu:16.04
## Specify one or more imagePullSecrets
##
## ref: https://kubernetes.io/docs/tasks/configure-pod-container/pull-image-private-registry/
##
# imagePullSecrets: []
## Specify the image pull policy: never, if-not-present, always. The cluster default will be used if not set.
##
imagePullPolicy: "if-not-present"
## Defines number of concurrent requests for new job from GitLab
## ref: https://docs.gitlab.com/runner/configuration/advanced-configuration.html#the-runners-section
## 限制來自GitLab的對新作業的並發請求數
requestConcurrency: 1
## Specify whether the runner should be locked to a specific project: true, false. Defaults to true.
##
locked: false
## Specify the tags associated with the runner. Comma-separated list of tags.
##
## ref: https://docs.gitlab.com/ce/ci/runners/#using-tags
##
tags: "kubernetes-runner,k8s"
## Specify if jobs without tags should be run.
## If not specified, Runner will default to true if no tags were specified. In other case it will
## default to false.
##
## ref: https://docs.gitlab.com/ce/ci/runners/#allowing-runners-with-tags-to-pick-jobs-without-tags
##
runUntagged: true
## Specify whether the runner should only run protected branches.
## Defaults to False.
##
## ref: https://docs.gitlab.com/ee/ci/runners/#protected-runners
##
protected: false
## Run all containers with the privileged flag enabled
## This will allow the docker:dind image to run if you need to run Docker
## commands. Please read the docs before turning this on:
## ref: https://docs.gitlab.com/runner/executors/kubernetes.html#using-docker-dind
##
privileged: true
## The name of the secret containing runner-token and runner-registration-token
# secret: gitlab-runner
## Namespace to run Kubernetes jobs in (defaults to the same namespace of this release)
##
# namespace:
## The amount of time, in seconds, that needs to pass before the runner will
## timeout attempting to connect to the container it has just created.
## ref: https://docs.gitlab.com/runner/executors/kubernetes.html
pollTimeout: 180
## Set maximum build log size in kilobytes, by default set to 4096 (4MB)
## ref: https://docs.gitlab.com/runner/configuration/advanced-configuration.html#the-runners-section
outputLimit: 4096
## Distributed runners caching
## ref: https://gitlab.com/gitlab-org/gitlab-runner/blob/master/docs/configuration/autoscale.md#distributed-runners-caching
##
## If you want to use s3 based distributing caching:
## First of all you need to uncomment General settings and S3 settings sections.
##
## Create a secret 's3access' containing 'accesskey' & 'secretkey'
## ref: https://aws.amazon.com/blogs/security/wheres-my-secret-access-key/
##
## $ kubectl create secret generic s3access \
## --from-literal=accesskey="YourAccessKey" \
## --from-literal=secretkey="YourSecretKey"
## ref: https://kubernetes.io/docs/concepts/configuration/secret/
##
## If you want to use gcs based distributing caching:
## First of all you need to uncomment General settings and GCS settings sections.
##
## Access using credentials file:
## Create a secret 'google-application-credentials' containing your application credentials file.
## ref: https://docs.gitlab.com/runner/configuration/advanced-configuration.html#the-runnerscachegcs-section
## You could configure
## $ kubectl create secret generic google-application-credentials \
## --from-file=gcs-application-credentials-file=./path-to-your-google-application-credentials-file.json
## ref: https://kubernetes.io/docs/concepts/configuration/secret/
##
## Access using access-id and private-key:
## Create a secret 'gcsaccess' containing 'gcs-access-id' & 'gcs-private-key'.
## ref: https://docs.gitlab.com/runner/configuration/advanced-configuration.html#the-runners-cache-gcs-section
## You could configure
## $ kubectl create secret generic gcsaccess \
## --from-literal=gcs-access-id="YourAccessID" \
## --from-literal=gcs-private-key="YourPrivateKey"
## ref: https://kubernetes.io/docs/concepts/configuration/secret/
cache: {}
## General settings
# cacheType: s3
# cachePath: "gitlab_runner"
# cacheShared: true
## S3 settings
# s3ServerAddress: s3.amazonaws.com
# s3BucketName:
# s3BucketLocation:
# s3CacheInsecure: false
# secretName: s3access
## GCS settings
# gcsBucketName:
## Use this line for access using access-id and private-key
# secretName: gcsaccess
## Use this line for access using google-application-credentials file
# secretName: google-application-credentials
## Build Container specific configuration
##
builds: {}
# cpuLimit: 200m
# memoryLimit: 256Mi
# cpuRequests: 100m
# memoryRequests: 128Mi
## Service Container specific configuration
##
services: {}
# cpuLimit: 200m
# memoryLimit: 256Mi
# cpuRequests: 100m
# memoryRequests: 128Mi
## Helper Container specific configuration
##
helpers: {}
# cpuLimit: 200m
# memoryLimit: 256Mi
# cpuRequests: 100m
# memoryRequests: 128Mi
# image: gitlab/gitlab-runner-helper:x86_64-latest
## Service Account to be used for runners
##
# serviceAccountName:
## If Gitlab is not reachable through $CI_SERVER_URL
##
# cloneUrl:
## Specify node labels for CI job pods assignment
## ref: https://kubernetes.io/docs/concepts/configuration/assign-pod-node/
##
# nodeSelector: {}
## Specify pod labels for CI job pods
##
# podLabels: {}
## Specify annotations for job pods, useful for annotations such as iam.amazonaws.com/role
# podAnnotations: {}
## Configure environment variables that will be injected to the pods that are created while
## the build is running. These variables are passed as parameters, i.e. `--env "NAME=VALUE"`,
## to `gitlab-runner register` command.
##
## Note that `envVars` (see below) are only present in the runner pod, not the pods that are
## created for each build.
##
## ref: https://docs.gitlab.com/runner/commands/#gitlab-runner-register
##
# env:
# NAME: VALUE
## Configure securitycontext
## ref: http://kubernetes.io/docs/user-guide/security-context/
##
securityContext:
fsGroup: 65533
runAsUser: 100
## Configure resource requests and limits
## ref: http://kubernetes.io/docs/user-guide/compute-resources/
##
resources: {}
# limits:
# memory: 256Mi
# cpu: 200m
# requests:
# memory: 128Mi
# cpu: 100m
## Affinity for pod assignment
## Ref: https://kubernetes.io/docs/concepts/configuration/assign-pod-node/#affinity-and-anti-affinity
##
affinity: {}
## Node labels for pod assignment
## Ref: https://kubernetes.io/docs/user-guide/node-selection/
##
nodeSelector: {}
# Example: The gitlab runner manager should not run on spot instances so you can assign
# them to the regular worker nodes only.
# node-role.kubernetes.io/worker: "true"
## List of node taints to tolerate (requires Kubernetes >= 1.6)
## Ref: https://kubernetes.io/docs/concepts/configuration/taint-and-toleration/
##
tolerations: []
# Example: Regular worker nodes may have a taint, thus you need to tolerate the taint
# when you assign the gitlab runner manager with nodeSelector or affinity to the nodes.
# - key: "node-role.kubernetes.io/worker"
# operator: "Exists"
## Configure environment variables that will be present when the registration command runs
## This provides further control over the registration process and the config.toml file
## ref: `gitlab-runner register --help`
## ref: https://docs.gitlab.com/runner/configuration/advanced-configuration.html
##
# envVars:
# - name: RUNNER_EXECUTOR
# value: kubernetes
## list of hosts and IPs that will be injected into the pod's hosts file
hostAliases: []
# Example:
# - ip: "127.0.0.1"
# hostnames:
# - "foo.local"
# - "bar.local"
# - ip: "10.1.2.3"
# hostnames:
# - "foo.remote"
# - "bar.remote"
## Annotations to be added to manager pod
##
podAnnotations: {}
# Example:
# iam.amazonaws.com/role: <my_role_arn>
## Labels to be added to manager pod
##
podLabels: {}
# Example:
# owner.team: <my_cool_team>
## HPA support for custom metrics:
## This section enables runners to autoscale based on defined custom metrics.
## In order to use this functionality, Need to enable a custom metrics API server by
## implementing "custom.metrics.k8s.io" using supported third party adapter
## Example: https://github.com/directxman12/k8s-prometheus-adapter
##
#hpa: {}
# minReplicas: 1
# maxReplicas: 10
# metrics:
# - type: Pods
# pods:
# metricName: gitlab_runner_jobs
# targetAverageValue: 400m
部署chart
## 創建runner
root@k8s-master71u:~# helm install gitlab-runner --namespace test ./gitlab-runner
NAME: gitlab-runner
LAST DEPLOYED: Sun Mar 31 09:40:46 2024
NAMESPACE: test
STATUS: deployed
REVISION: 1
TEST SUITE: None
NOTES:
Your GitLab Runner should now be registered against the GitLab instance reachable at: "http://192.168.1.55/"
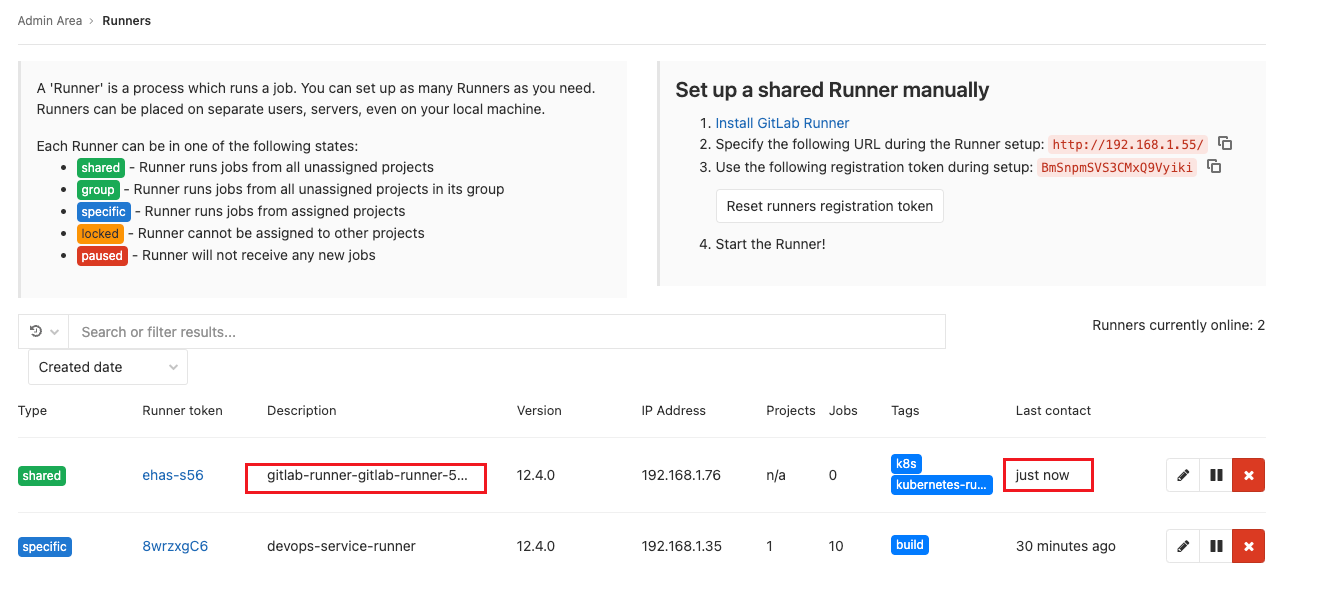
此時可以回到Gitlab頁面,查看runner是否已註冊
確定已註冊成功了
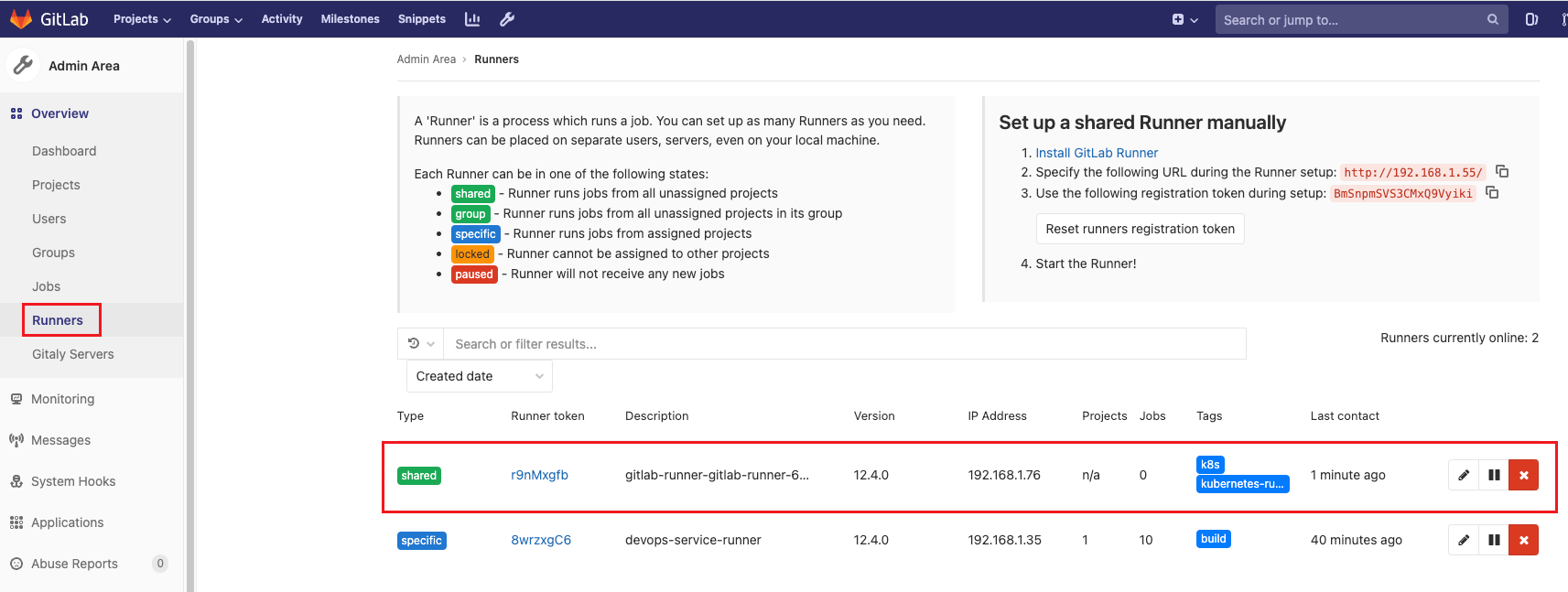
進k8s查看,可以看到namespace test下,已經有一個runner產生
root@k8s-master71u:~/gitlab-runner# kubectl get pod -n test
NAME READY STATUS RESTARTS AGE
gitlab-runner-gitlab-runner-648b664dbf-knshw 1/1 Running 0 3m57s
測試 Runner 執行pipeline
在專案新增一個名為.gitlab-ci.yml的檔案
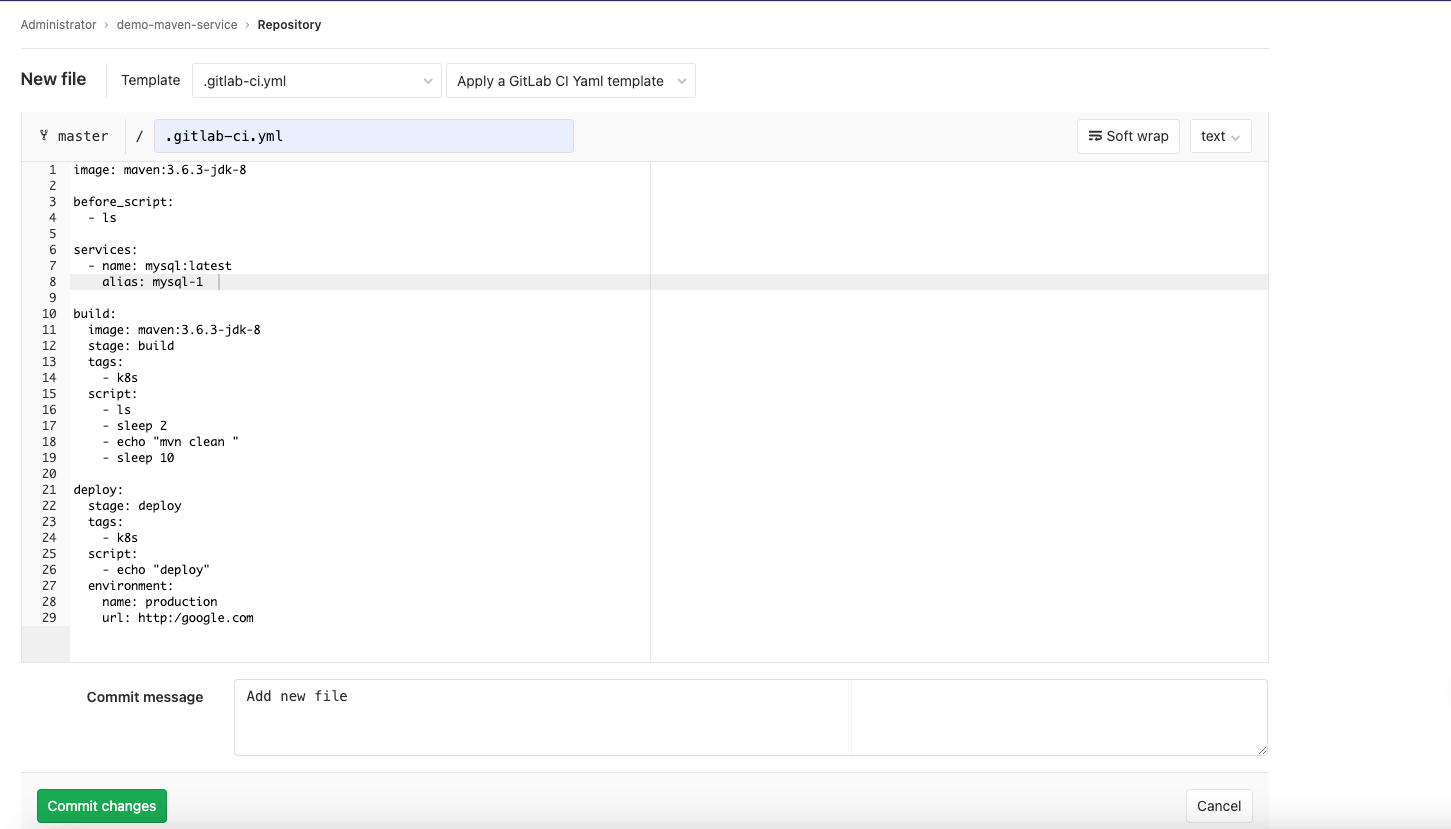
image: maven:3.6.3-jdk-8
before_script:
- ls
services:
- name: mysql:latest
alias: mysql-1
build:
image: maven:3.6.3-jdk-8
stage: build
tags:
- k8s
script:
- ls
- sleep 2
- echo "mvn clean "
- sleep 10
deploy:
stage: deploy
tags:
- k8s
script:
- echo "deploy"
environment:
name: production
url: http:/google.com
調整Runner設定,並分配給Project使用

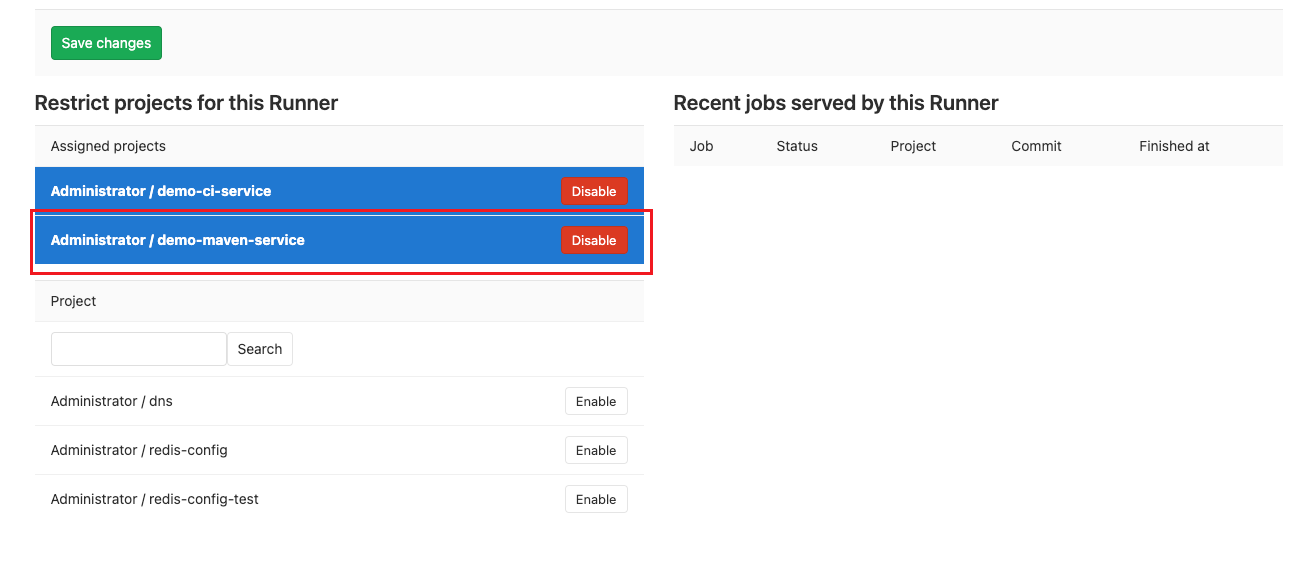
執行pipeline
看到dns無法解析
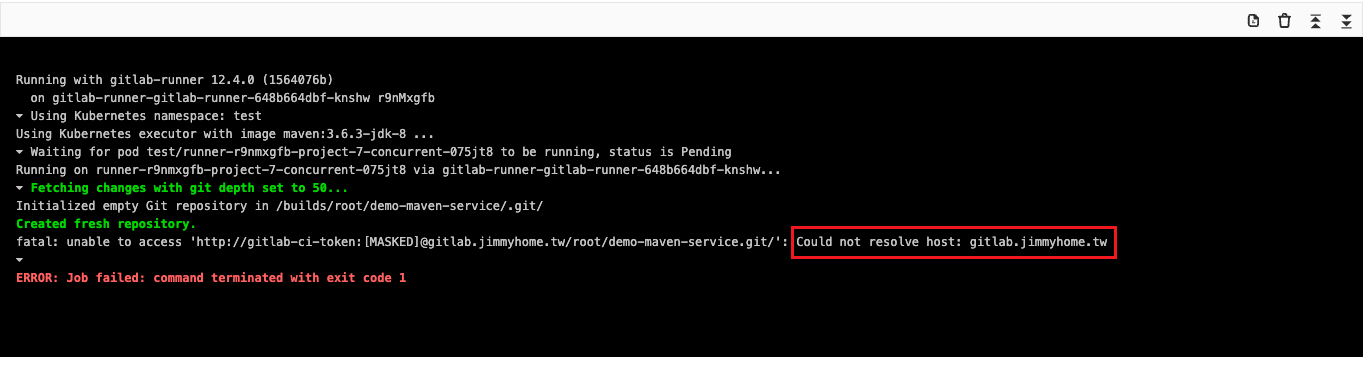
coredns添加hosts解析
root@k8s-master71u:~# kubectl get configmaps coredns -n kube-system -o yaml > coredns-configmaps.yaml
root@k8s-master71u:~# vim coredns-configmaps.yaml
apiVersion: v1
data:
Corefile: |
.:53 {
errors {
}
health {
lameduck 5s
}
ready
kubernetes cluster.local in-addr.arpa ip6.arpa {
pods insecure
fallthrough in-addr.arpa ip6.arpa
}
hosts {
192.168.1.55 gitlab.jimmyhome.tw
fallthrough
}
root@k8s-master71u:~# kubectl apply -f coredns-configmaps.yaml
重啟coredns服務
root@k8s-master71u:~# kubectl delete pod coredns-57c7559cc8-sq8c4 -n kube-system
pod "coredns-57c7559cc8-sq8c4" deleted
root@k8s-master71u:~# kubectl delete pod coredns-57c7559cc8-vrf7g -n kube-system
pod "coredns-57c7559cc8-vrf7g" deleted
root@k8s-master71u:~# kubectl get pod -n kube-system
NAME READY STATUS RESTARTS AGE
cadvisor-8ksn8 1/1 Running 3 (19h ago) 93d
cadvisor-zxskk 1/1 Running 3 (19h ago) 93d
calico-kube-controllers-777ff6cddb-xbmt2 1/1 Running 5 (19h ago) 13d
calico-node-5gfmb 1/1 Running 1 (19h ago) 13d
calico-node-7vxfv 1/1 Running 1 (19h ago) 13d
calico-node-cpxc6 1/1 Running 1 (19h ago) 13d
calico-node-k7xmf 1/1 Running 1 (19h ago) 13d
calico-node-x5fhs 1/1 Running 1 (19h ago) 13d
coredns-57c7559cc8-7ktfj 1/1 Running 0 25s
coredns-57c7559cc8-hzxfv 1/1 Running 0 8s
再一次重新執行pipeline
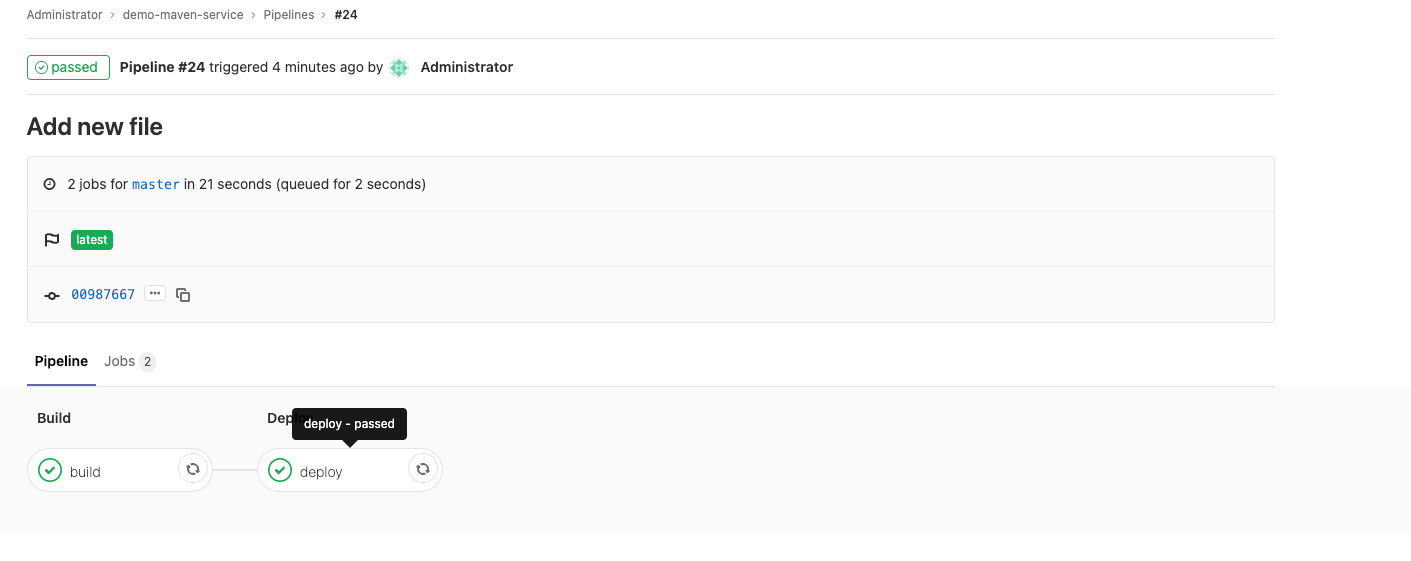
執行pipeline時,k8s裡面會產生executor pod來執行任務
# 產生 executor,執行任務
root@k8s-master71u:~# kubectl get pod -n test
NAME READY STATUS RESTARTS AGE
gitlab-runner-gitlab-runner-648b664dbf-knshw 1/1 Running 0 26m
runner-r9nmxgfb-project-7-concurrent-0chf72 3/3 Running 0 3s
# 執行完畢,executor 自動delete掉
root@k8s-master71u:~# kubectl get pod -n test
NAME READY STATUS RESTARTS AGE
gitlab-runner-gitlab-runner-648b664dbf-knshw 1/1 Running 0 26m
runner-r9nmxgfb-project-7-concurrent-0chf72 2/3 Error 0 4s
# executor消失
root@k8s-master71u:~# kubectl get pod -n test
NAME READY STATUS RESTARTS AGE
gitlab-runner-gitlab-runner-648b664dbf-knshw 1/1 Running 0 26m
可以看到,確定是使用,我們分配的runner執行

解決構建快取問題
所謂的構建快取就是我們在進行maven等構建工具打包時所依賴的包。預設會在私服中獲取,加快構建速度可以在本地快取一份。在此,我們需要創建PVC來持久化構建快取,加速構建速度。為了節省儲存空間決定不在每個項目中儲存構建快取,而是配置全局快取。
創建pvc

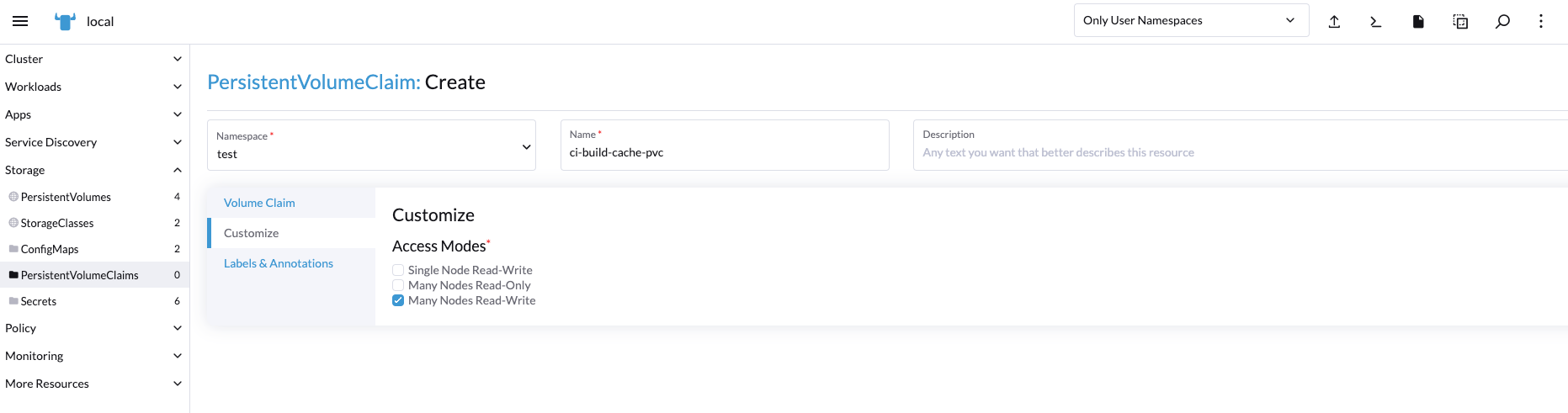
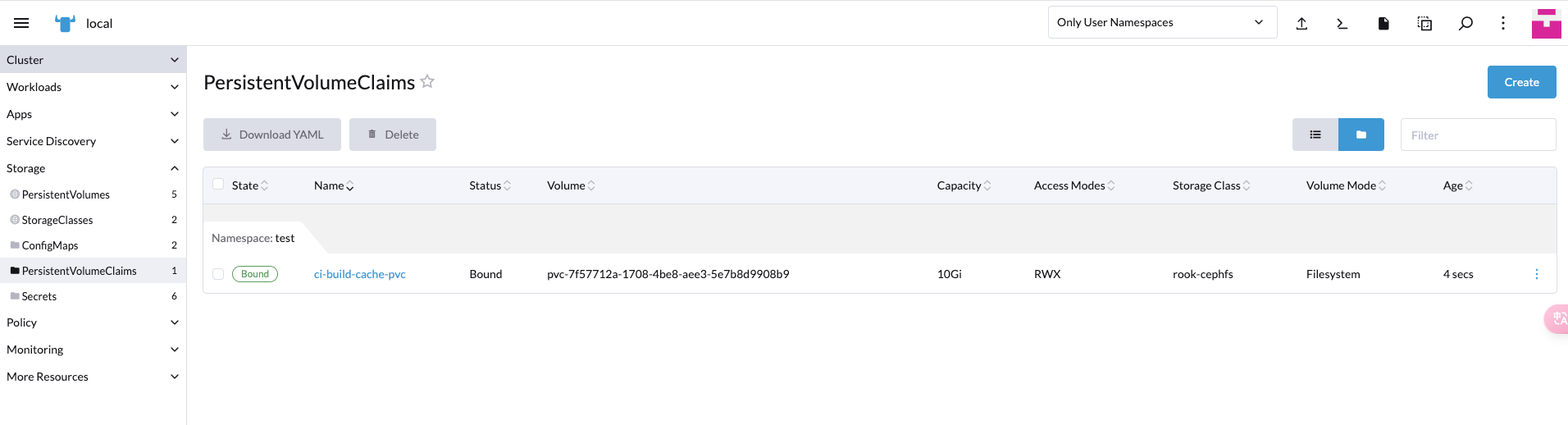
第一步:編輯value.yml文件,添加構建快取資訊配置。
root@k8s-master71u:~/gitlab-runner# vim values.yaml
## 當停止管道時等待其作業終止時間
terminationGracePeriodSeconds: 3600
## configure build cache
cibuild:
cache:
pvcName: ci-build-cache-pvc
mountPath: /home/gitlab-runner/ci-build-cache
第二步:編輯templates/configmap.yml文件,entrypoint部分添加runner配置。在start之前添加,這樣runner在創建構建pod的時候會根據配置掛載pvc。
root@k8s-master71u:~/gitlab-runner# vim templates/configmap.yaml
# add build cache
cat >>/home/gitlab-runner/.gitlab-runner/config.toml <<EOF
[[runners.kubernetes.volumes.pvc]]
name = "{{.Values.cibuild.cache.pvcName}}"
mount_path = "{{.Values.cibuild.cache.mountPath}}"
EOF
# Start the runner
exec /entrypoint run --user=gitlab-runner \
--working-directory=/home/gitlab-runner
到此gitlab-runner chart部分配置就完成了,接下來可以通過Helm命令進行創建和更新了。
root@k8s-master71u:~# helm upgrade gitlab-runner --namespace test ./gitlab-runner
Release "gitlab-runner" has been upgraded. Happy Helming!
NAME: gitlab-runner
LAST DEPLOYED: Sun Mar 31 11:10:46 2024
NAMESPACE: test
STATUS: deployed
REVISION: 6
TEST SUITE: None
NOTES:
Your GitLab Runner should now be registered against the GitLab instance reachable at: "http://192.168.1.55/"
root@k8s-master71u:~# kubectl get pod -n test
NAME READY STATUS RESTARTS AGE
gitlab-runner-gitlab-runner-7c4f66c9bb-jkg96 1/1 Running 0 59s
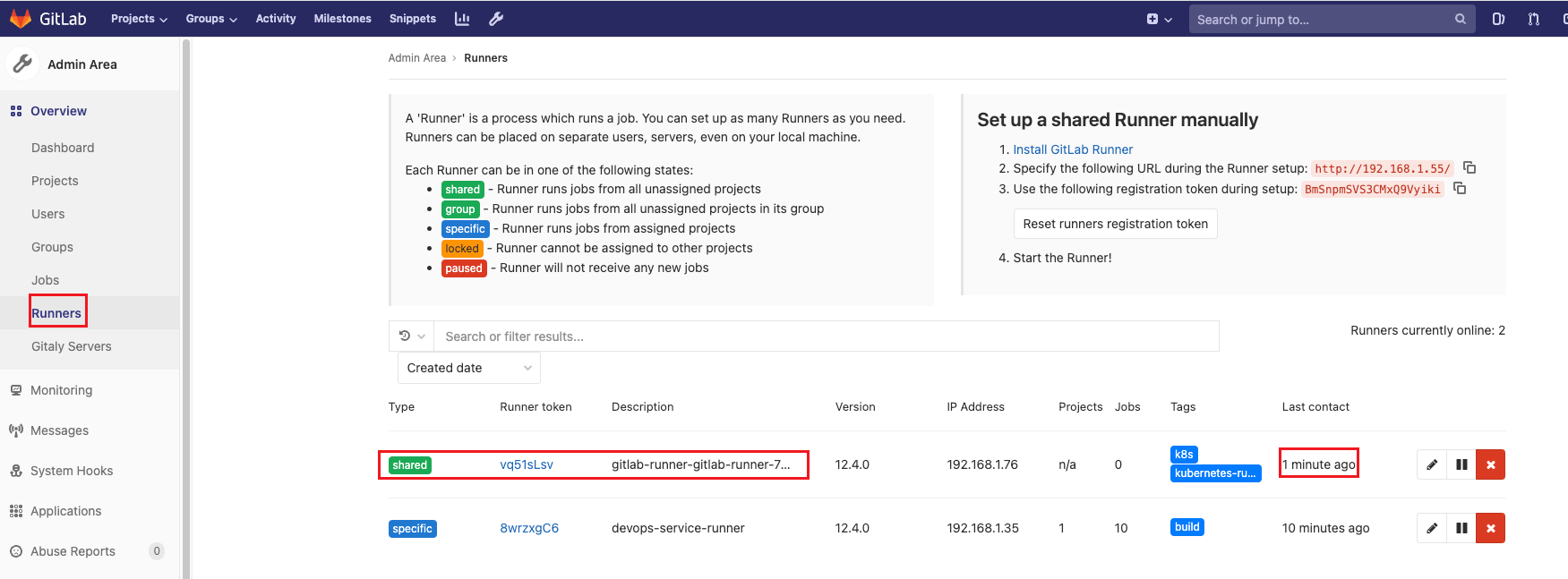
構建測試
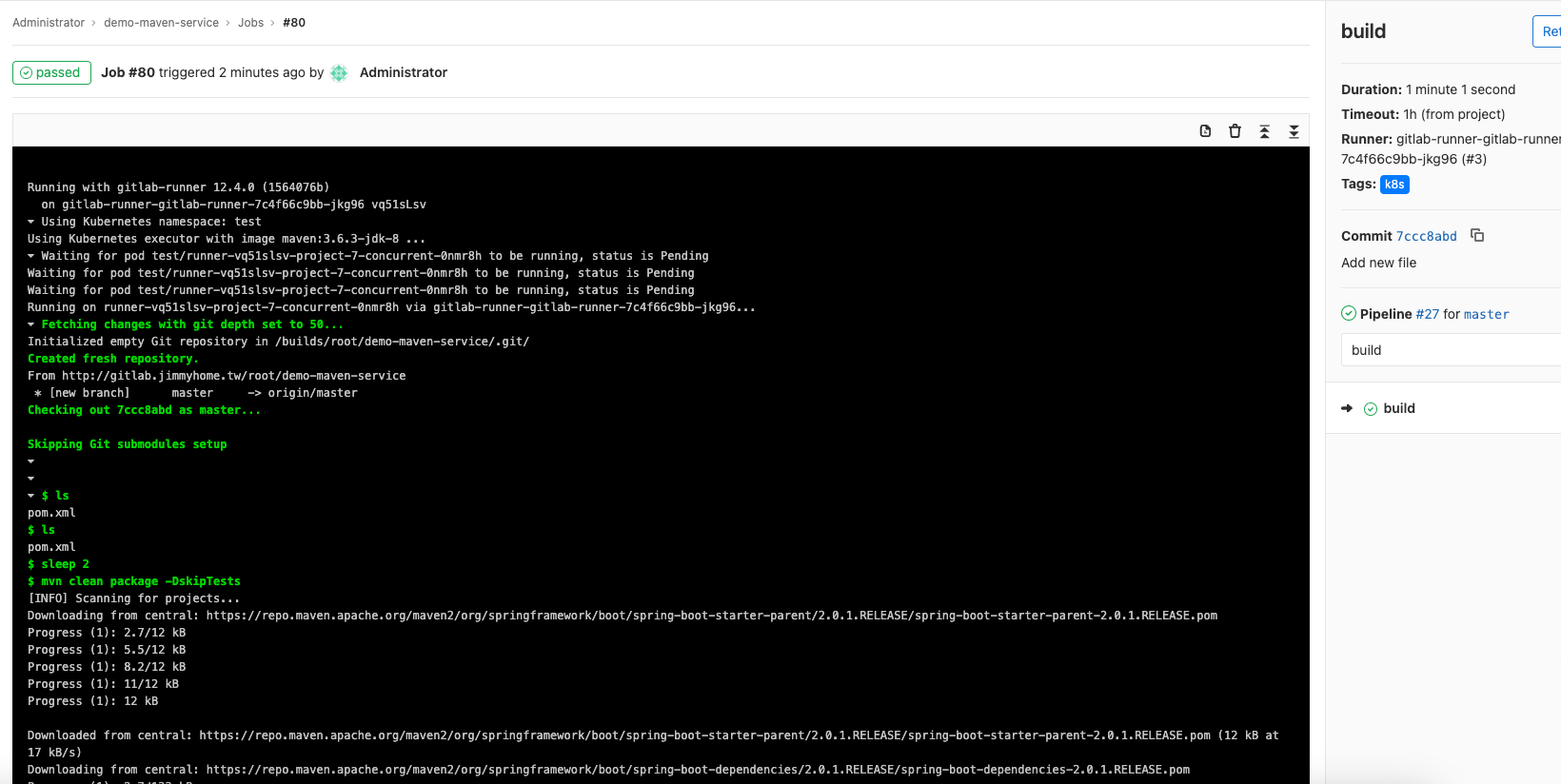
可以看到executor,確實有掛載pvc
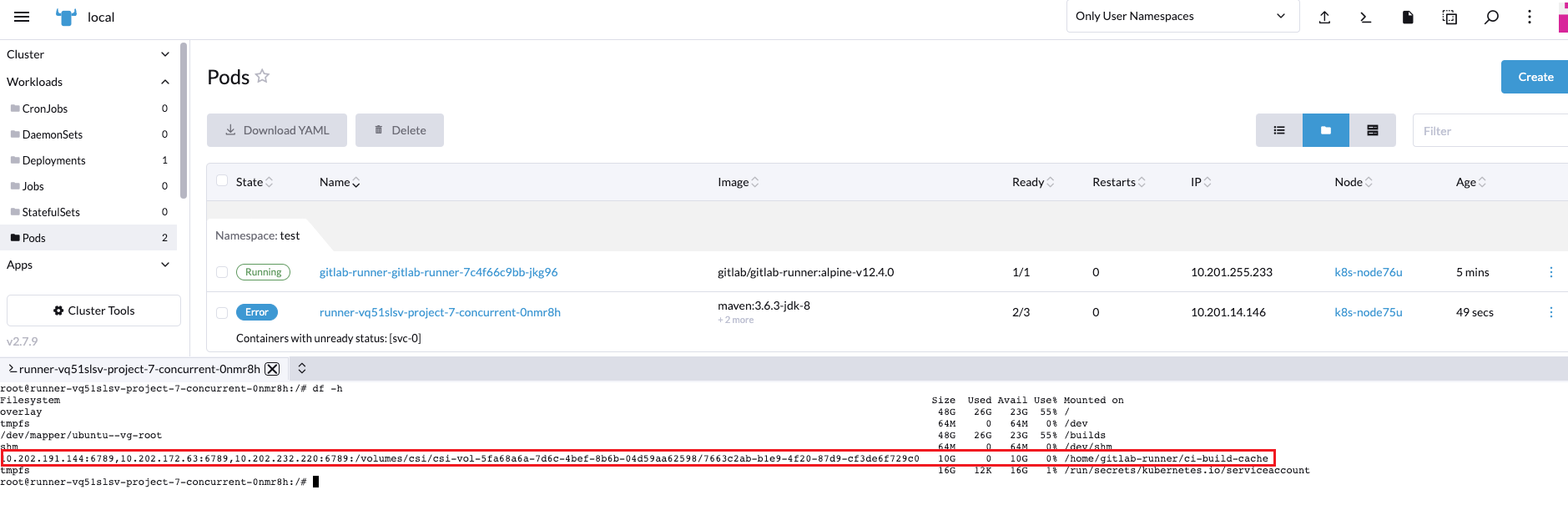
部署完成了,後續使用構建工具打包時添加指定快取目錄。例如:maven
mvn clean package -DskipTests -Dmaven.repo.local=/home/gitlab-runner/ci-build-cache/maven
.gitlab-ci.yml
image: maven:3.6.3-jdk-8
before_script:
- ls
services:
- name: mysql:latest
alias: mysql-1
build:
image: maven:3.6.3-jdk-8
stage: build
tags:
- k8s
script:
- ls
- sleep 2
- mvn clean package -DskipTests -Dmaven.repo.local=/home/gitlab-runner/ci-build-cache/maven
- sleep 10
deploy:
stage: deploy
tags:
- k8s
script:
- echo "deploy"
environment:
name: production
url: http:/google.com

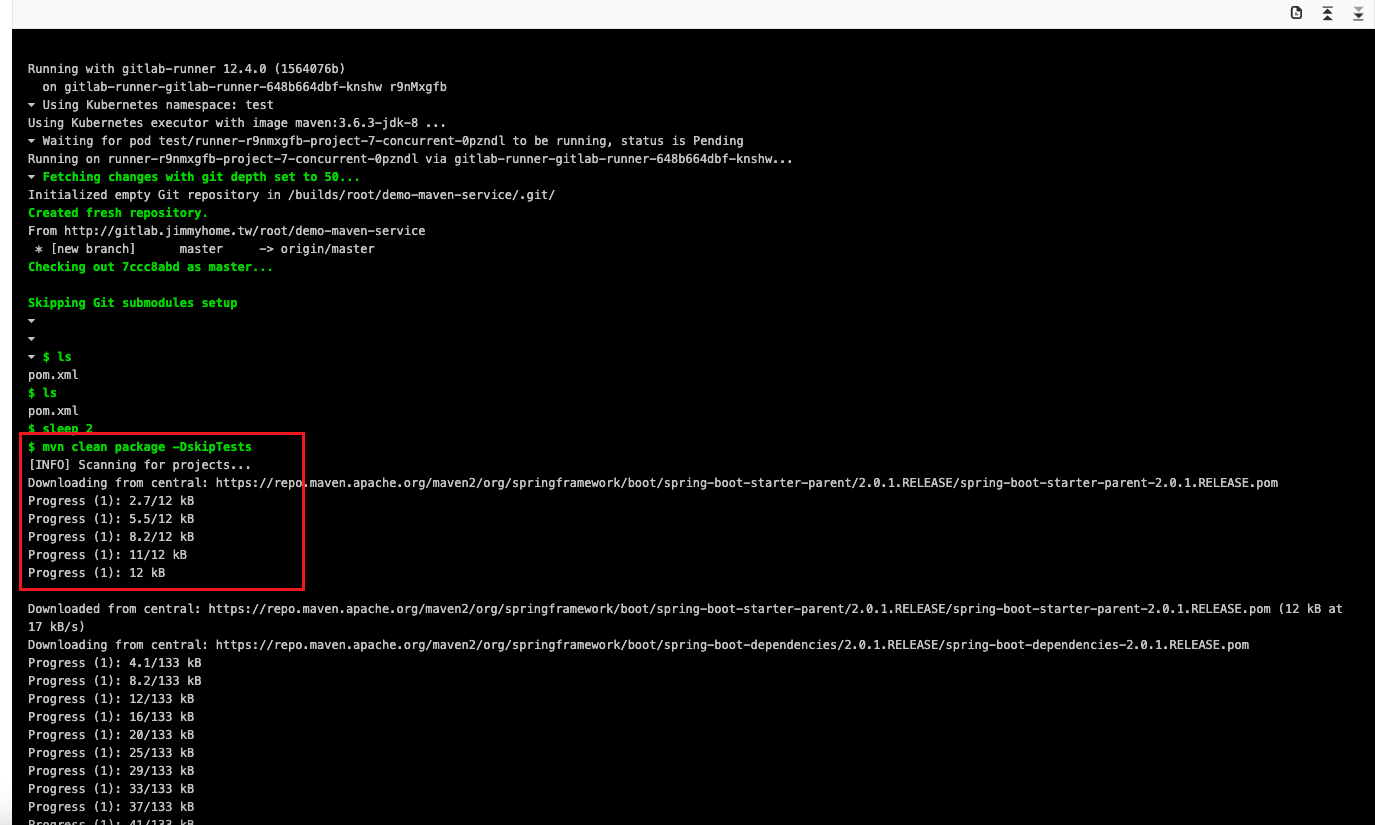
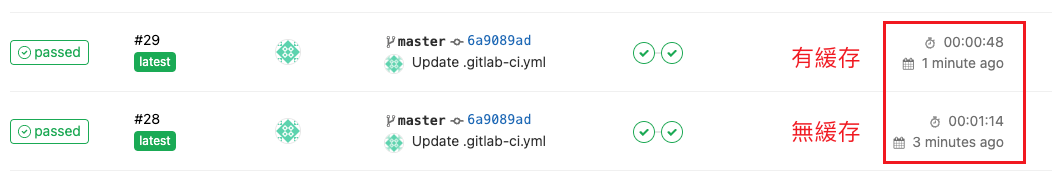
可以看到,已經有緩存了,不會再去下載

可以看到有緩存和無緩存,pipeline執行時間上確實有差
查看緩存檔案,是否真的存在pvc中
root@k8s-master71u:~# ceph-fuse -m 10.202.172.63:6789,10.202.232.220:6789,10.202.191.144:6789 /mnt/mycephfs
root@k8s-master71u:~# cd /mnt/mycephfs/volumes/csi/csi-vol-5fa68a6a-7d6c-4bef-8b6b-04d59aa62598/7663c2ab-b1e9-4f20-87d9-cf3de6f729c0/maven
root@k8s-master71u:/mnt/mycephfs/volumes/csi/csi-vol-5fa68a6a-7d6c-4bef-8b6b-04d59aa62598/7663c2ab-b1e9-4f20-87d9-cf3de6f729c0/maven# ll
total 8
drwxr-xr-x 15 root root 34573465 Mar 31 11:22 ./
drwxr-xr-x 3 root root 34573465 Mar 31 11:22 ../
drwxr-xr-x 3 root root 333176 Mar 31 11:22 backport-util-concurrent/
drwxr-xr-x 3 root root 798096 Mar 31 11:22 ch/
drwxr-xr-x 3 root root 44925 Mar 31 11:22 classworlds/
drwxr-xr-x 6 root root 3187173 Mar 31 11:22 com/
drwxr-xr-x 3 root root 429136 Mar 31 11:22 commons-io/
drwxr-xr-x 4 root root 20095 Mar 31 11:22 io/
drwxr-xr-x 4 root root 146461 Mar 31 11:22 javax/
drwxr-xr-x 3 root root 338878 Mar 31 11:22 junit/
drwxr-xr-x 3 root root 1006247 Mar 31 11:22 mysql/
drwxr-xr-x 3 root root 4997 Mar 31 11:22 net/
drwxr-xr-x 18 root root 28229427 Mar 31 11:22 org/
drwxr-xr-x 3 root root 7896 Mar 31 11:22 xmlpull/
drwxr-xr-x 3 root root 26958 Mar 31 11:22 xpp3/
root@k8s-master71u:~# umount /mnt/mycephfs
解決構建製品問題
在kubernetes中對cache支持一般,我們可以使用artifacts進行代替。但是考慮到artifacts收集製品會占用儲存空間,所以準備研究下如何配置統一的快取。實際上我們可以將repo目錄做成持久化。
經過測試,在使用kubernetes執行器創建的構建pod會默認掛載一個空目錄。此目錄用於儲存每次下載的代碼,因為是空目錄的原因導致後續測試pod無法獲取需要重新下載代碼,這還不要緊,重要的是構建生成的文件target目錄都不存在了導致後續步驟接連失敗。
問題演示 : 每個stages,都會重新下載代碼,導致上一個流程編譯完產生的target,在下一個stages,不會存在,如果要測試其功能,就無法執行

image: maven:3.6.3-jdk-8
before_script:
- ls
services:
- name: mysql:latest
alias: mysql-1
build:
image: maven:3.6.3-jdk-8
stage: build
tags:
- k8s
script:
- ls
- sleep 2
- mvn clean package -DskipTests -Dmaven.repo.local=/home/gitlab-runner/ci-build-cache/maven
- sleep 10
- ls target/
test:
image: maven:3.6.3-jdk-8
stage: test
tags:
- k8s
script:
- ls target/
- sleep 2
- mvn test -Dmaven.repo.local=/home/gitlab-runner/ci-build-cache/maven
- sleep 10
deploy:
stage: deploy
tags:
- k8s
script:
- echo "deploy"
environment:
name: production
url: http:/google.com
build流程,是有target目錄
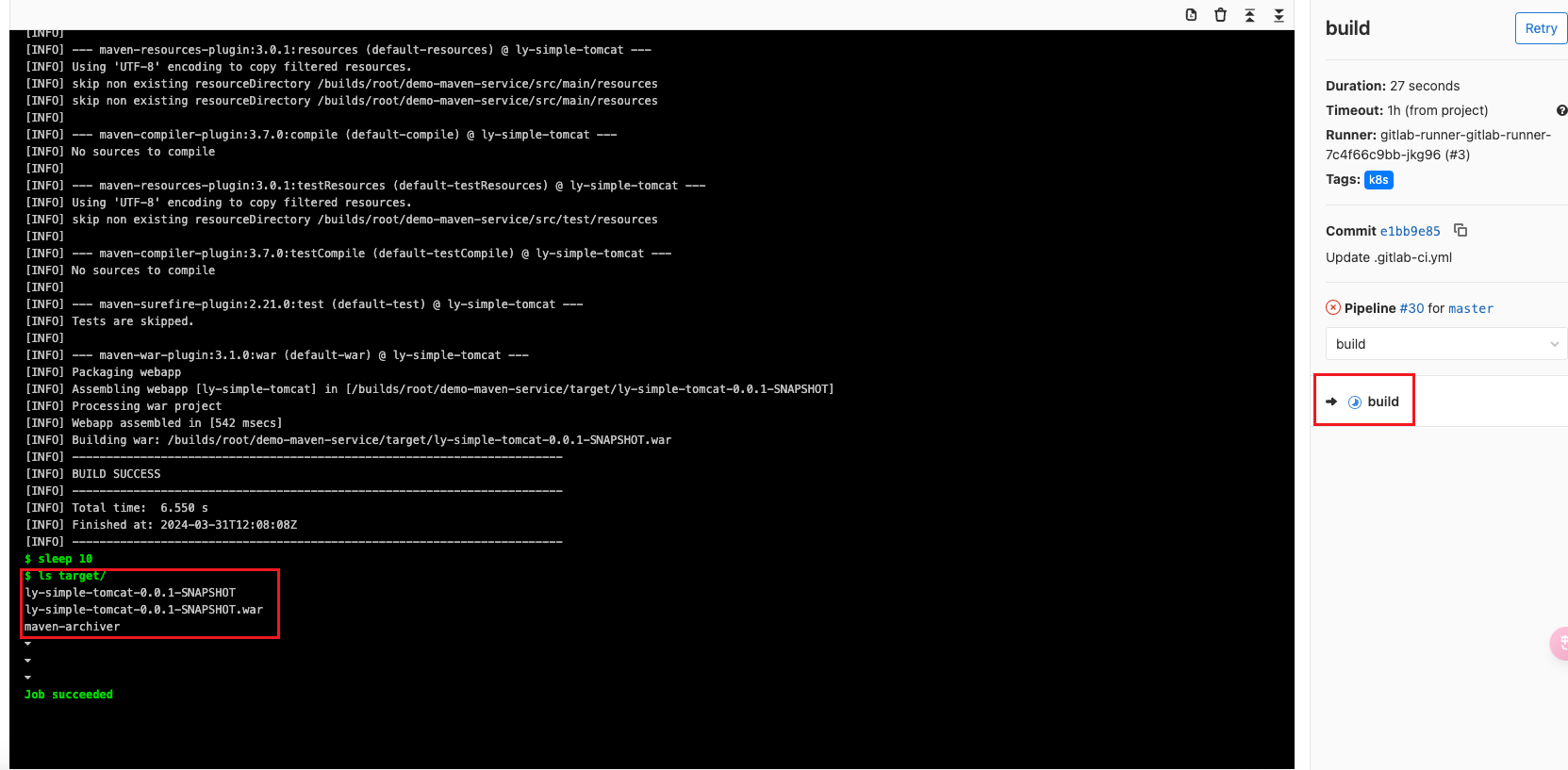
test流程,是沒有target目錄

經過測試在本地的pv中能夠看到,下載的代碼文件。但是默認每次每個job運行的時候都會獲取遠程最新的代碼,會把構建目錄刪除掉,此時就需要配置git checkout策略了。其實按照我們目前的場景,不需要每個作業都下載代碼。只要第一個作業下載好最新的代碼,然後運行流水線即可。當在運行流水線的過程中遇到新代碼提交可以放到下次流水線執行。
需要在ci文件中定義GIT_CHECKOUT變數,預設值為true,即每次都需要代碼下載。我們將全局配置為false然後在build作業中配置為true。也就實現了只在build作業下載最新代碼了。
GIT_CHECKOUT: "false"
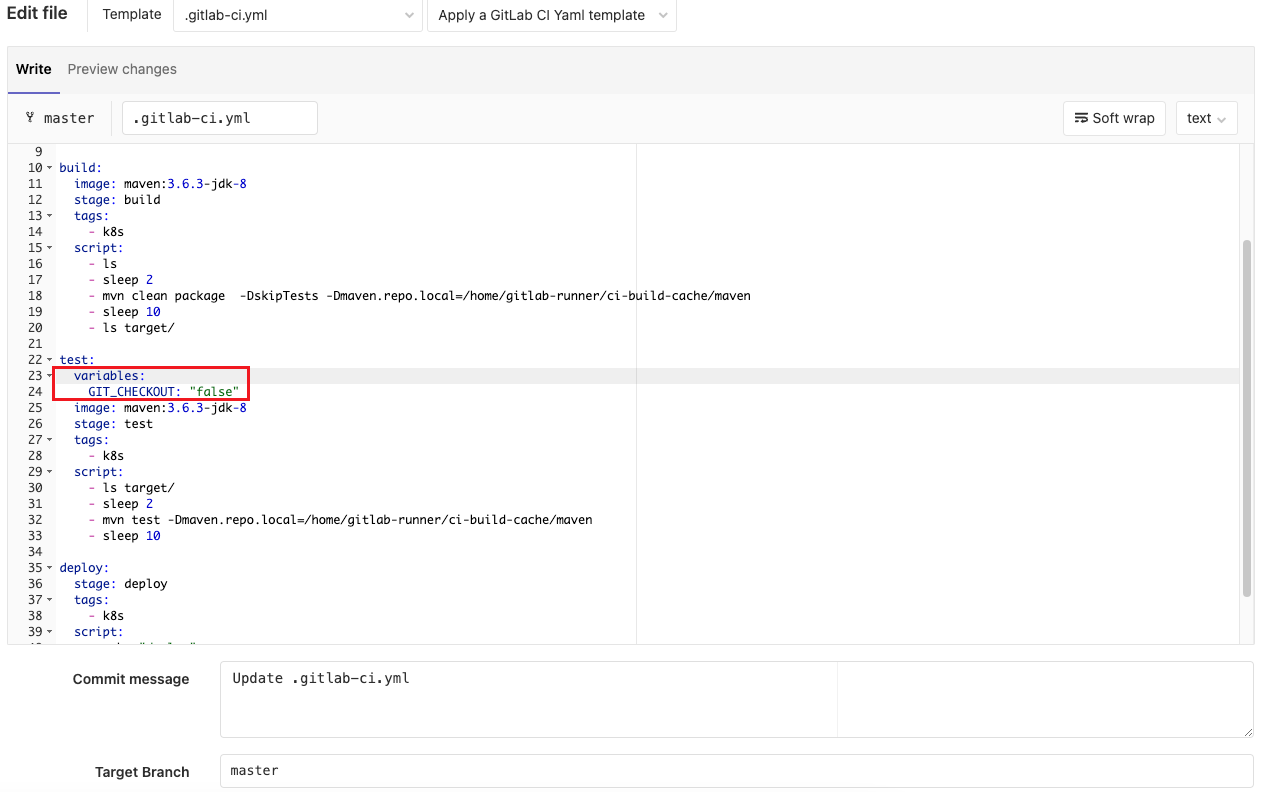
image: maven:3.6.3-jdk-8
before_script:
- ls
services:
- name: mysql:latest
alias: mysql-1
build:
image: maven:3.6.3-jdk-8
stage: build
tags:
- k8s
script:
- ls
- sleep 2
- mvn clean package -DskipTests -Dmaven.repo.local=/home/gitlab-runner/ci-build-cache/maven
- sleep 10
- ls target/
test:
variables:
GIT_CHECKOUT: "false"
image: maven:3.6.3-jdk-8
stage: test
tags:
- k8s
script:
- ls target/
- sleep 2
- mvn test -Dmaven.repo.local=/home/gitlab-runner/ci-build-cache/maven
- sleep 10
deploy:
stage: deploy
tags:
- k8s
script:
- echo "deploy"
environment:
name: production
url: http:/google.com
可以看到,就算不重新下載代碼,一樣不會有target,因為使用kubernetes執行器創建的構建pod會默認掛載一個空目錄。

創建repo持久化pvc

編譯values.yaml文件添加註冊配置變數。RUNNER_BUILDS_DIR定義構建目錄。CUSTOM_BUILD_DIR_ENABLED開啟自訂構建目錄配置。
添加repo目錄快取配置,我們把自訂的構建目錄放到默認構建目錄的下面builds目錄中。
root@k8s-master71u:~/gitlab-runner# vim values.yaml
## configure build cache
cibuild:
cache:
pvcName: ci-build-cache-pvc
mountPath: /home/gitlab-runner/ci-build-cache
builds:
pvcName: ci-build-dir-pvc
mountPath: /home/gitlab-runner/ci-build-dir/builds
## Configure environment variables that will be present when the registration command runs
## This provides further control over the registration process and the config.toml file
## ref: `gitlab-runner register --help`
## ref: https://docs.gitlab.com/runner/configuration/advanced-configuration.html
##
# envVars:
# - name: RUNNER_EXECUTOR
# value: kubernetes
envVars:
- name: RUNNER_BUILDS_DIR
value: "/home/gitlab-runner/ci-build-dir/"
- name: CUSTOM_BUILD_DIR_ENABLED
value: true
編輯templates/configmap.yml
root@k8s-master71u:~/gitlab-runner# vim templates/configmap.yaml
# add build cache
cat >>/home/gitlab-runner/.gitlab-runner/config.toml <<EOF
[[runners.kubernetes.volumes.pvc]]
name = "{{.Values.cibuild.cache.pvcName}}"
mount_path = "{{.Values.cibuild.cache.mountPath}}"
[[runners.kubernetes.volumes.pvc]]
name = "{{.Values.cibuild.builds.pvcName}}"
mount_path = "{{.Values.cibuild.builds.mountPath}}"
EOF
更新runner
root@k8s-master71u:~# helm upgrade gitlab-runner --namespace test ./gitlab-runner
Release "gitlab-runner" has been upgraded. Happy Helming!
NAME: gitlab-runner
LAST DEPLOYED: Sun Mar 31 12:30:59 2024
NAMESPACE: test
STATUS: deployed
REVISION: 7
TEST SUITE: None
NOTES:
Your GitLab Runner should now be registered against the GitLab instance reachable at: "http://192.168.1.55/"
root@k8s-master71u:~# kubectl get pod -n test
NAME READY STATUS RESTARTS AGE
gitlab-runner-gitlab-runner-59cb5fc9df-zfwb5 1/1 Running 0 28s
在CI文件中配置,如果不開啟自訂構建目錄配置會出現錯誤。
variables:
GIT_CLONE_PATH: $CI_BUILDS_DIR/builds/$CI_PROJECT_NAMESPACE/$CI_PROJECT_NAME/$CI_PIPELINE_ID
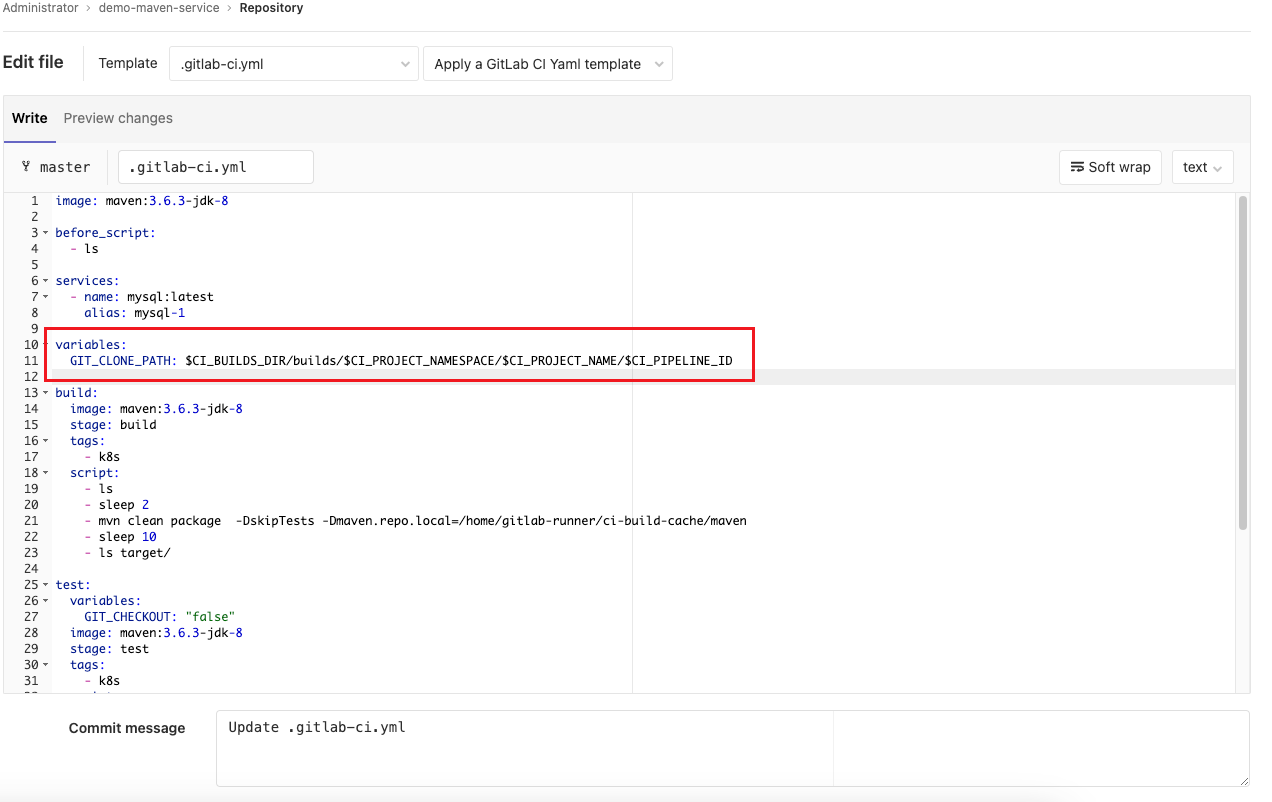
image: maven:3.6.3-jdk-8
before_script:
- ls
services:
- name: mysql:latest
alias: mysql-1
variables:
GIT_CLONE_PATH: $CI_BUILDS_DIR/builds/$CI_PROJECT_NAMESPACE/$CI_PROJECT_NAME/$CI_PIPELINE_ID
build:
image: maven:3.6.3-jdk-8
stage: build
tags:
- k8s
script:
- ls
- sleep 2
- mvn clean package -DskipTests -Dmaven.repo.local=/home/gitlab-runner/ci-build-cache/maven
- sleep 10
- ls target/
test:
variables:
GIT_CHECKOUT: "false"
image: maven:3.6.3-jdk-8
stage: test
tags:
- k8s
script:
- ls target/
- sleep 2
- mvn test -Dmaven.repo.local=/home/gitlab-runner/ci-build-cache/maven
- sleep 10
deploy:
stage: deploy
tags:
- k8s
script:
- echo "deploy"
environment:
name: production
url: http:/google.com
可以看到,test流程有上一個流程build出來的target目錄
